Posted by - Komal Sharma -
on - 8 hours ago -
Filed in - Business -
Access Control as a Service (ACaaS) Access Control as a Service (ACaaS) Market Access Control as a Service (ACaaS) Market Size -
7 Views - 0 Comments - 0 Likes - 0 Reviews
In an era where digital transformation is reshaping every industry, physical and digital security must also evolve. Traditional access control systems - once reliant on on-premise servers, physical key cards, and localized management - are rapidly being replaced by cloud-based solutions. One of the most innovative of these is Access Control as a Service (ACaaS), a subscription-based model that delivers flexible, scalable, and cost-effective security management.
Access Control as a Service (ACaaS) is a cloud-based security model that delivers access control functionality through a subscription service rather than traditional on-premises systems. It enables organizations to manage and monitor physical or digital access rights remotely using the internet, providing centralized control, scalability, and real-time updates. ACaaS reduces the need for expensive hardware and maintenance while enhancing flexibility and integration with other cloud services.
Access Control as a Service (ACaaS) is a cloud-based security solution that allows organizations to manage who can access specific locations, systems, or data—without the need for expensive, on-site hardware or software. Instead of purchasing, installing, and maintaining a traditional access control system, businesses subscribe to a service hosted and maintained by a third-party provider.
This model shifts the responsibility for updates, backups, and cybersecurity from the organization to the service provider. ACaaS offers a centralized platform, accessible via web or mobile applications, enabling administrators to monitor and control access in real-time from anywhere in the world.
The core principle of ACaaS is simple: security infrastructure is hosted in the cloud rather than on-premises. Here’s a breakdown of how it typically works:
Cloud-Based Platform – All access control data (credentials, permissions, activity logs) is stored and managed in the provider’s secure cloud environment.
Physical Devices – Entry points are equipped with card readers, biometric scanners, or mobile access systems, which communicate with the cloud to verify user credentials.
Subscription Model – Businesses pay a monthly or annual fee based on features, number of users, or number of doors being secured.
Remote Management – Administrators can grant or revoke access, set up permissions, and view real-time activity logs from a web dashboard or mobile app.
Users can control and monitor security from any internet-connected device, eliminating the need to be physically present.
ACaaS can easily expand as businesses grow, accommodating new users, locations, or security levels without major hardware overhauls.
Service providers handle software updates and security patches, ensuring the system stays up-to-date with the latest features and protections.
Detailed logs and analytics provide visibility into access patterns, helping organizations detect anomalies and improve security protocols.
Many ACaaS platforms integrate with video surveillance, visitor management systems, and identity management platforms for a unified security approach.
Traditional access control systems often require a significant upfront investment in servers, hardware, and IT resources. ACaaS operates on a subscription model, drastically reducing capital expenditures (CapEx) and shifting costs to operational expenses (OpEx).
Because ACaaS providers maintain and monitor the infrastructure, businesses benefit from enterprise-grade cybersecurity, redundancy, and disaster recovery protocols that may otherwise be cost-prohibitive.
Security administrators can manage multiple facilities or locations from a single dashboard. This level of centralized control is particularly valuable for multi-site organizations like retail chains, healthcare networks, or corporate campuses.
With fewer hardware requirements and pre-configured cloud environments, ACaaS solutions can be deployed more quickly than traditional systems—sometimes in days rather than weeks or months.
Many ACaaS platforms support mobile credentials, allowing employees to use smartphones for access. This eliminates the need for physical cards or keys, reducing costs associated with replacements and lost credentials.
ACaaS eliminates the need for dedicated IT security staff while providing enterprise-level protection at an affordable rate.
Multi-location companies benefit from centralized access management, real-time monitoring, and seamless scalability.
These businesses require dynamic access control to accommodate a constantly changing roster of tenants and visitors.
Hospitals and clinics need strict access control to safeguard sensitive areas and patient data while complying with regulations like HIPAA.
Schools and universities can use ACaaS to secure buildings, labs, and dormitories while offering mobile credentials for students and staff.
While ACaaS offers numerous advantages, it’s important to address potential concerns:
Internet Dependency – Since ACaaS operates in the cloud, reliable internet connectivity is essential for optimal performance.
Data Privacy & Compliance – Organizations must ensure that providers comply with industry regulations (e.g., GDPR, HIPAA).
Vendor Reliability – Selecting a reputable service provider with robust security infrastructure and uptime guarantees is critical.
AI and ML are being incorporated into ACaaS platforms to enable predictive analytics, detect unusual access patterns, and proactively identify potential security threats. This trend will lead to smarter, self-learning systems that can adapt to changing security environments.
The shift toward contactless solutions is accelerating the adoption of mobile credentials and biometric authentication methods such as facial recognition, fingerprint scanning, and voice ID. These methods enhance user convenience while improving security.
ACaaS is increasingly being integrated with Internet of Things (IoT) devices, enabling real-time data exchange between access control systems, surveillance cameras, and building automation technologies for a seamless security experience.
As businesses move away from traditional infrastructure, fully cloud-native ACaaS platforms are gaining traction. These solutions offer improved scalability, easier deployment, and reduced maintenance costs compared to hybrid systems.
With data privacy regulations such as GDPR, HIPAA, and CCPA becoming stricter, ACaaS providers are investing heavily in encryption, identity management, and compliance-ready frameworks to meet global standards.
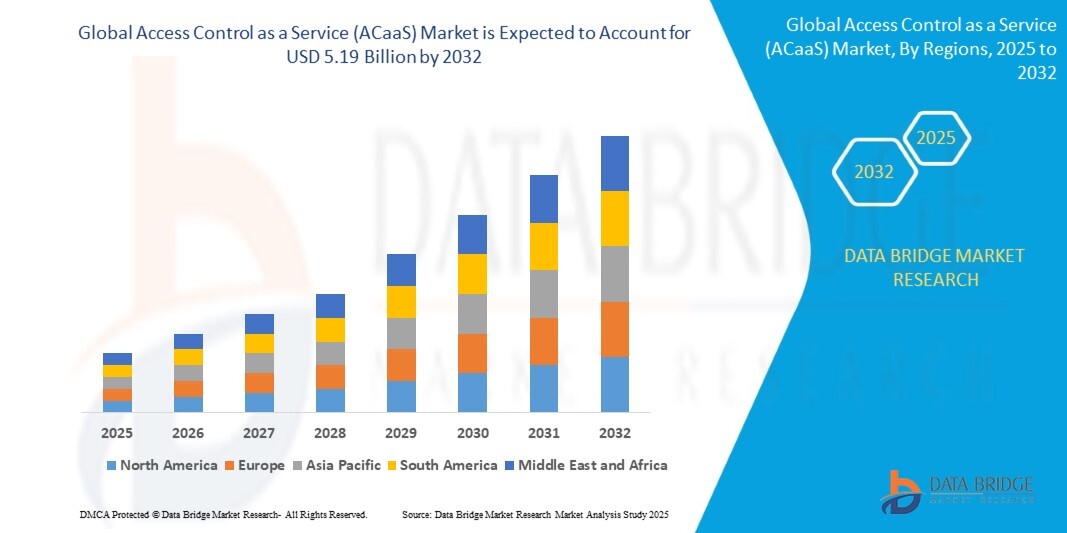
According to Data Bridge Market Research, the size of the global access control as a service (ACaaS) market was estimated at USD 1.51 billion in 2024 and is projected to grow at a compound annual growth rate (CAGR) of 16.70% to reach USD 5.19 billion by 2032.
Learn More: https://www.databridgemarketresearch.com/reports/global-access-control-as-a-service-acaas-market
Access Control as a Service (ACaaS) is more than just a trend - it’s a fundamental shift in how organizations approach security. By leveraging the power of the cloud, ACaaS provides flexibility, scalability, and enhanced protection, all while reducing costs and simplifying management. Whether you’re a small business owner or managing a global enterprise, embracing ACaaS can ensure that your security systems are as dynamic and forward-thinking as the world around you.

Our Mission... “To assist disaster survivors by providing a source for them to come together in time of need, to aid in the listing of events, information and other forms of assistance, and continuing support through the recovery process.”

Share this page with your family and friends.